| benf.org : other : rapsody |
The Rapsody N35 is a follow up to the RSH 100 media center - this time it's got HD support, better codecs (the RSH 100 got quite upset when you rewound stuff...), and a network device.... (which is by far the best upgrade).
It can mount any SMB share it sees on the local network, and can export its own contents as an NDAS device; NDAS is a wacky proprietary NAS technology from XiMeta.
Unfortunately, NDAS is a bit of a pain, as the windows drivers don't support any form of discovery, and in order to attach to the device, you have to enter a 20 digit key, and another 5 digit key to get write access. (and, on my rapsody at least, these are printed in an utterly unreadable font, and underneath the device. What a pain).
However... NDAS devices seem (taking 2 rapsodys as an exhaustive sample :) to send out what I'll term NDAS HELO packets every 2.5 seconds - these are 64 byte Ethernet packets with a frame id of 88ad (ximeta).
and... it turns out that the NDAS ID, and the write key are simply functions of the MAC address. (The N35 seems, oddly, to have 2 addresses; the official one [written on the device, used for NDAS], and another used for TCP, which is 1 higher..)

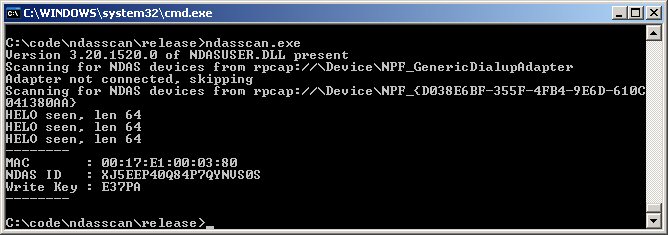
So, here is a (pretty hacky) NDAS network scanner - it will list all the NDAS devices on your subnet (by waiting for 5s, during which at least 1 NDAS HELO is broadcast), and use the functions provided in the NDAS source code (released by IOCELL) to generate the NDAS ID / Write key.
Requires:I have moved this onto github - find it at https://github.com/leibnitz27/ndasscan
Run on the command line with
ndasscan.exeto hunt for ndas devices.
Alternately, if you know the MAC you want to get the id/key for, simply provide that as the first command line argument - i.e.
ndasscan 00:17:E1:00:03:80
Originally, NDASscan required that the NDAS binaries be installed - this is because the NDAS code was closed source, so NDASscan had to call into specific, determined points in the NDAS binaries to call the key generation routines.
IOCELL have now open sourced this code - this means I can simply include the actual code I was calling all along, rather than rely on finding it in the NDASUSER.DLL binary.
For archaeological purposes, the original code for ndasscan is here, and the original binary is here. I don't see any reason for them to be used any more.
Since I no longer have to rely on windows binaries, there's no reason not to build this for linux as well. I don't have my N35 available now, so haven't yet done this, but if you want to generalise the git repos above, feel free to send me a pull request. Or if you're super desperate, and that last sentence means nothing to you, drop me a line.
Last updated 2014 |